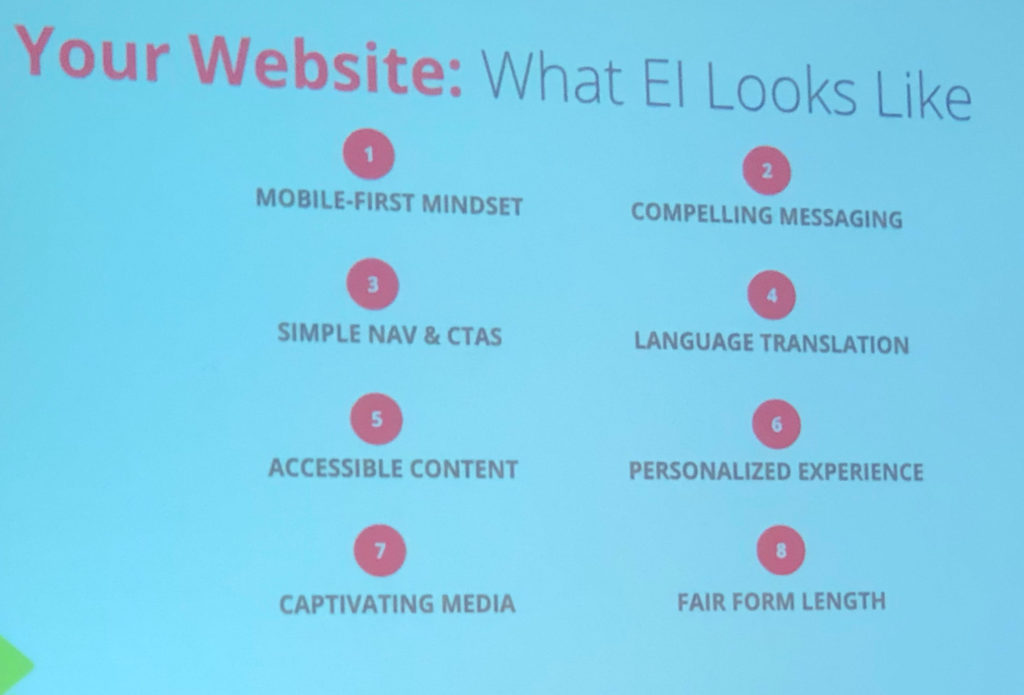
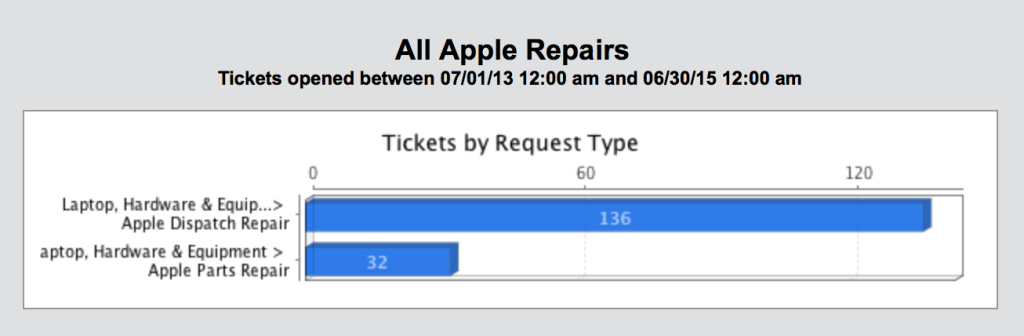
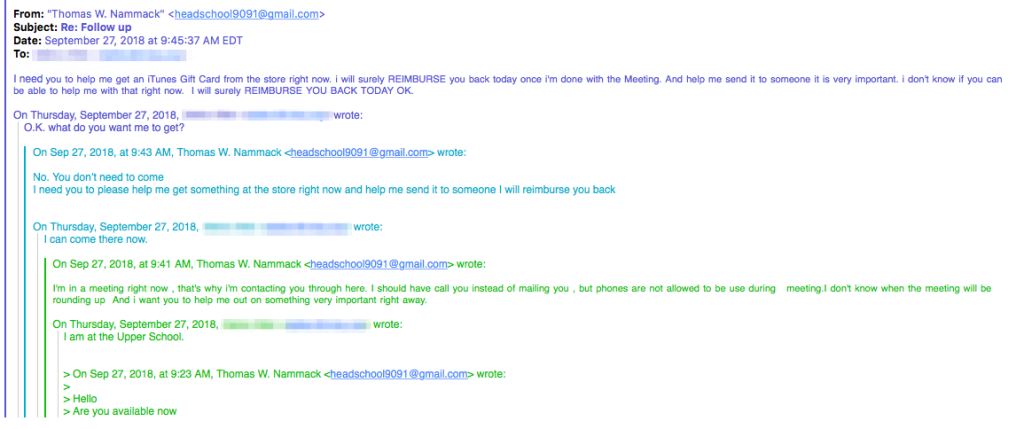
There is a lot of talk about what school is going to look like in September and a lot of questions that have come with it.
Will we open online? What will our schedule look like? Will we have some kids or teachers in the building and some at home? Blended? Hybrid? Synchronous? Asynchronous? The questions go on and on…
One clear thing is that we will be using some form of technology to connect people that are in one place to those in another. With this, there are many hardware pieces to consider and how they will fit a school’s unique learning plan.
What all of these technologies will have in common is they will all need a platform to run on and bandwidth to make it all connect.
You may be using ZOOM, Google Meet, WebEx, or Teams… whatever it is you use, there are bandwidth requirements for each of these.
As we are all doing remote learning from home, the bandwidth requirements may not be all that noticeable. You may see a slow down while someone is working, and someone else is streaming a movie, on YouTube, playing Fortnite. Still, nothing like you will know when you are in school and have multiple classrooms all trying to connect to their own video stream for two-way communications.
Before you get started on all of these plans, it will be essential to get a better understanding of if you’re ready for these bandwidth requirements, and there are a few things to consider to get started.
Continue reading →